What is SOC 2
SOC 2 is a data security compliance standard developed by the American Institute of CPAs (AICPA). The standard focuses on the secure handling and management of customer data. SOC 2 reports are most commonly utilized by service providers. For any business or organization, SOC 2 compliance is a powerful way to show customers and prospects that it is committed to protecting their data and they have the procedures in place to do so effectively.
Achieving a Successful SOC 2 Report
Organizations need to make several decisions leading up to their SOC 2 audit regarding the report types, the scope of their audit, and what CPA firm to work with.
There are two different SOC 2 reports, Type 1 and Type 2.
Type 1 report: Describes a vendor’s environment and whether the security control design is suitable to meet relevant principles. This report is a point-in-time evaluation of the design of a security program.
Type 2 report: Tests the operational effectiveness of those systems and their controls over a period of time. This report is an evaluation of the execution of a security program.
The SOC 2 Type 2 is the more valuable report because it demonstrates a greater commitment to data security. The Type 1 report could be a good option for businesses or organizations working towards a security certification for the first time.
SOC 2 is more flexible than other security frameworks because it allows organizations to design and implement their own controls. The standard focuses on the 5 AICPA Trust Service Principles: Security, Availability, Confidentiality, Processing Integrity, and Privacy.
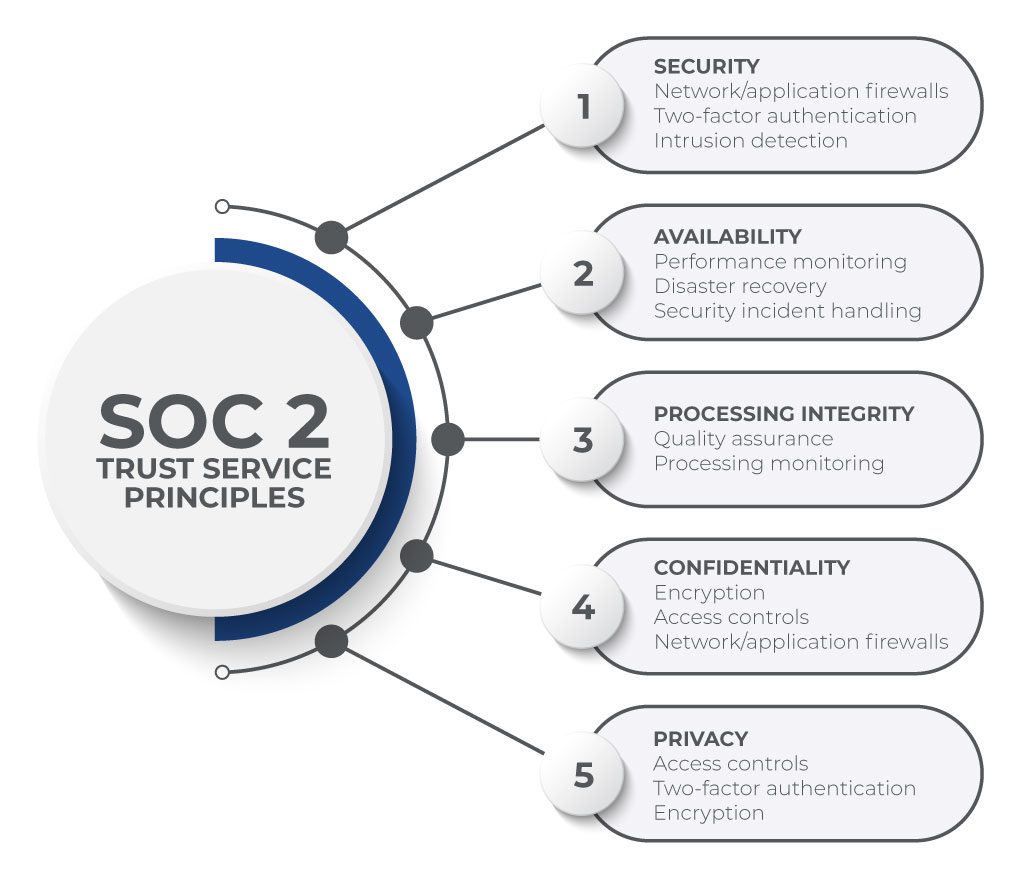
The Security principle is required for all organizations. When crafting a scope, organizations need to identify which of the remaining principles are relevant to their operations. Most organizations will need to include the Confidentiality principle in their scope.
When it’s time for your SOC 2 audit, it must be conducted by a licensed CPA that you select. The auditors will examine your security controls and issue a report with one of these opinions:
- Unqualified Opinion: The equivalent of a “pass.”
- Qualified Opinion: A mostly clean report but there was some sort of issue found. Organizations can proceed with a Qualified Opinion, opting to explain to customers and partners why the exception was rare and how it was fixed.
- Adverse Opinion: The equivalent of a “fail.”
- Disclaimer of Opinion: This happens when the required evidence wasn’t provided to the auditor.
There is no finish line for SOC 2 compliance. Annual audits are required to keep your report current. The annual audits are time-consuming tasks, especially for growing businesses. New customers, third-party vendors, employees, and contracts can result in the need for new controls. To learn more about ensuring your annual SOC 2 audits are successful, read our Maintain SOC 2 After Your Initial Report blog.
SOC 2 Compared to ISO 27001
SOC 2 and ISO 27001 are both popular information security frameworks. The standards share common goals, but the two have significant differences.
SOC 2 is highly regarded in North America but lacks recognition globally. On the other hand, ISO 27001 is an internationally recognized framework, making it a good option for businesses with a customer base overseas.
SOC 2 and ISO 27001 allow organizations to customize some of their scope based on their specific needs and operations. SOC 2 offers more flexibility because it doesn’t have a required set of controls.
Typically, ISO 27001 audits are more expensive than SOC 2 audits because they require additional documentation.
Read our ISO 27001 vs SOC 2 blog for a more in-depth comparison of the frameworks.
The Benefits of a SOC 2 Report
SOC 2 is a highly recognized attestation that can serve as a business driver. It allows organizations to demonstrate they have an effective, secure system in place for protecting data. A SOC 2 report will quickly gain the trust of customers by showing you are committed to information security.
How We Can Help
CompliancePoint has a full suite of services designed to guide organizations through every step of a successful SOC 2 attestation. Our experienced staff can help you design controls that will best fit your existing operations. Through our readiness assessment, you will learn what controls you are not satisfying, how to remediate any existing gaps, and what controls lack proper documentation. Once your organization has completed a successful audit, we can help manage your SOC 2 program on an ongoing basis to ensure your organization remains compliant.
Our independent CompliancePoint Assurance (CPA) firm can perform audits for a SOC 2 Type 1 and Type 2 report. Having CompliancePoint prepare your business for the SOC 2 audit performed by our CPA firm will streamline the process, saving you time and money.
Failure to comply with relevant requirements can have a devastating impact on your organization. Don't take chances, let our experts help.
Frequently Asked Questions
SOC 2 stands for System and Organization Control 2.
The five AICPA Trust Service Principles are Security, Availability, Confidentiality, Processing Integrity, and Privacy.
Organizations must go through a SOC 2 audit conducted by a licensed CPA. Auditors examine the organization’s security controls and issue a report with one of the following options:
- Unqualified Opinion: The equivalent of a “pass.”
- Qualified Opinion: A mostly clean report but there was some sort of issue found. Organizations can proceed with a Qualified Opinion, opting to explain to customers and partners why the exception was rare and how it was fixed.
- Adverse Opinion: The equivalent of a “fail.”
- Disclaimer of Opinion: This happens when the required evidence wasn’t provided to the auditor.
SOC 1 and SOC 2 are both compliance frameworks developed by the AICPA under the System and Organization Controls (SOC) framework, but they serve different purposes.
SOC 1 focuses on protecting and managing financial data. It is commonly used by organizations that impact their customers’ financial statements such as banks, payroll services companies, and other businesses that offer financial services.
SOC 2 is focused on protecting sensitive customer data. It is commonly used by SaaS companies, cloud providers, data centers, healthcare organizations, and IT security companies.

10 Billion+
Records Audited

150+
Cases as an
Expert Witness

2,500+
Companies Assessed





