What’s New with PCI DSS v4.0
It’s official, the new version of the PCI DSS has been released by the Payment Card Industry Security Standards Council! PCI DSS v4.0 is the next evolution of the standard that addresses emerging risks and technologies and enables innovative methods to combat new threats as the industry’s security needs continue to evolve.
Goals of the PCI DSS v4.0 and what’s new:
Continuing to meet the security needs of the payment card industry. Security practices must evolve with the changing threat landscape. The new version of the standard has changed by expanding the multi-factor authentication requirements, updating the password requirements inline with current best practices and adding new controls to address e-commerce and phishing risk.
Promoting security as a continuous process. The new version focuses on the establishment of clearly assigned roles and responsibilities for each requirement and includes guidance to help implement and maintain security processes and new reporting options around areas of improvement, providing more transparency in reporting.
Adding flexibility for different methodologies. Under certain conditions the new version of the standard allows for the use of group, shared and generic accounts. Risk-based discussions can now be made by organizations when establishing frequencies for certain recurring tasks. The use of customized approaches is now allowed for validated requirements, allowing additional fixability for new and emerging technologies.
Enhancing validation methods. The new version includes clear validation options and reporting granularity supporting better report transparency with improvements to the alignment between information reported in and between formal Reports on Compliance (ROC) and the Self-Assessment Questionnaire (SAQ).
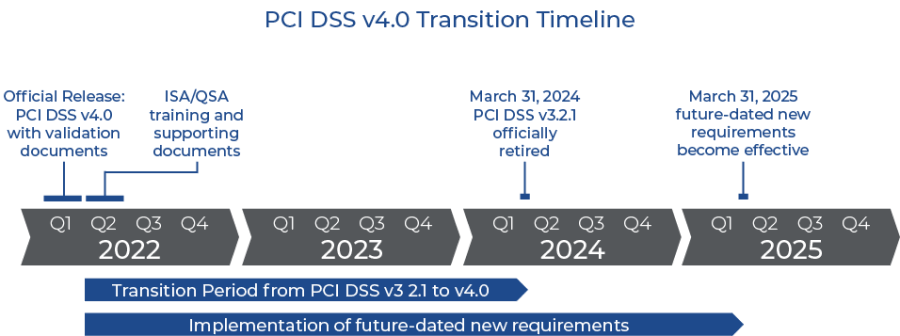
How long do you have to transition to the 4.0 standard?
Organizations may assess to either PCI DSS v4.0 or PCI DSS v3.2.1 for the next two years as they complete training and implement the new requirements of v4.0. v3.2.1 will officially be retired at the end of March 2024.
What new control requirements are effective immediately for v4.0?
There are four main themes for the control requirements that are effective immediately under v4.0 assessments:
- Clearly defined roles and responsibilities within each requirement area
- A risk analysis for any customized approaches
- Scope is documented and confirmed annually
- Third Party Service Providers (TPSP) must facilitate customer requests for a roles and responsibilities matrix between the TPSP and the customer
| New Requirement | Comments | |
| 3.1.2 | Roles and responsibilities for performing activities in Requirement 3 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • Data retention and disposal policies (including SAD) • PAN Masking • Controlling PAN movement • PAN encryption at rest • Cryptographic Key Management. |
| 4.1.2 | Roles and responsibilities for performing activities in Requirement 4 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • Encryption in Transit (Open or Public Networks) |
| 5.1.2 | Roles and responsibilities for performing activities in Requirement 5 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • AV and Malware Configurations • AV/Malware Management & Monitoring • Anti-Phishing |
| 6.1.2 | Roles and responsibilities for performing activities in Requirement 6 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • Software Development • Vulnerability Management • Web Application Security • Change Management |
| 7.1.2 | Roles and responsibilities for performing activities in Requirement 7 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • Access Control |
| 8.1.2 | Roles and responsibilities for performing activities in Requirement 8 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • User Management • Authentication • Multi-Factor Remote Access |
| 9.1.2 | Roles and responsibilities for performing activities in Requirement 9 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • Physical Access Control • Physical Personnel and Visitor Management • Visitor Logs • Offline Media & Backups Logs and Inventory • POI Device Management |
| 10.1.2 | Roles and responsibilities for performing activities in Requirement 10 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • Log Management, Monitoring and Retention • Log Configuration • NTP Configuration |
| 11.1.2 | Roles and responsibilities for performing activities in Requirement 11 are documented, assigned, and understood. | Ensure roles and responsibilities have been formally document and signed to Employees. Ensure these employees understand their responsibilities. Documented assignments should cover the following policies and procedures: • Wire Access Point Management and Monitoring • Wireless Inventory • Vulnerability Management • Penetration Testing • Network IDS and File Integrity • Change Management |
| 12.3.2 | A targeted risk analysis is performed for each PCI DSS requirement that is met with the customized approach. | Organization must preform a targeted risk analysis for each control requirement that utilizes a customized approach. This process must include the following: • Documented evidence specified in Appendix D • Approval by senior management • Evaluation every 12 months |
| 12.5.2 | PCI DSS scope is documented and confirmed at least once every 12 months. | Organization must document and confirm the scope of their PCI DSS environment annually and when any significant change occurs. This documentation must include the following: • All data flows • All locations where account data is stored, processed, or transmitted • All system components • All segmentation Controls • All third party connections • Confirmation that everything has been identified |
| 12.9.2 | TPSPs support customers’ requests to provide PCI DSS compliance status and information about PCI DSS requirements that are the responsibility of the TPSP. | TPSPs support their customers’ requests for information to meet Requirements 12.8.4 and 12.8.5 by providing the following upon customer request: • PCI DSS compliance status information for any service the TPSP performs on behalf of customers (Requirement 12.8.4). • Information about which PCI DSS requirements are the responsibility of the TPSP and which are the responsibility of the customer, including any shared responsibilities (Requirement 12.8.5). |
For more information, check out our common pitfalls when managing your PCI Program and our PCI DSS blog series that breaks down the standards by requirement area.
CompliancePoint is a Qualified Security Assessor Company (QSAC). Our consultants have decades of experience as practitioners and auditors. Please reach out to us at connect@compliancepoint.com if you have any questions about how CompliancePoint can assist your organization with preparing for your PCI DSS Certification.
Finding a credible expert with the appropriate background, expertise, and credentials can be difficult. CompliancePoint is here to help.